Today’s Cyber Risk Landscape for Architecture, Engineering and Construction
You may not immediately recognize the need for data security, password management or disaster recovery as an organization in the Architecture, Engineering and Construction (AEC) industry, but COVID-19 has led to more malicious activity and a sharp increase in cybercrime. Eighty percent of firms have seen a rise in cyberattacks this past year. The FBI has reported a 400% increase in cybercrimes since the start of the pandemic, with nearly half of all cyberattacks committed against small business.
What’s been happening in the last 12 to 18 months? The pandemic has had a major impact on all organizations, resulting in employees working remotely and IT departments identifying how best to serve and support a mobile workforce. Additionally, prior existing factors driving organizations to transition to the cloud have been accelerated by the crisis as companies urgently look for scalable and cost-effective off-premise technology solutions. The real question is not what has been happening due to COVID, but what have organizations done differently regarding cybersecurity?
Many organizations were heavily focused on supporting the employee and enabling remote connectivity to networks, email, and third-party platforms. Few organizations deliberately considered adjustments to protect their data and systems. Instead, some relaxed security controls and protocols to reduce stress on their mobile workforce, such as reducing or eliminating password changes, performing less than robust patching of end-user workstations, failing to implement multi-factor authentication for remote access, and not assessing where documents are stored. Specifically for the AEC industry, the need to share drawings and information with multiple contractors is a critical requirement. However, when sharing documents on third-party platforms, such as Dropbox and Google Drive, are organizations verifying that the data is secure and authorized to be posted online?
When data is insecure, cybercriminals attack, particularly during a pandemic. COVID created an increase in anxiety and fear among Americans; scammers were some of the first to respond and specifically attacked the AEC industry. Proofpoint®, one of the market leaders in email security, revealed that the AEC industry is the second most targeted for email fraud with an average of 61 attacks per company over a three-month period. Additionally, those orchestrating attacks are aware that construction is a very lucrative, high cash-flow business, which makes AEC even more appealing to criminals.
What are the trends and techniques we are seeing today?
Today, it is easier to move money than ever before. Hence, business email compromise is a top risk for those in the AEC industry. There are several ways criminal organizations look to move money outside of your enterprise:
Bogus Invoice Scheme from Third Party
The most successful form of attack is a bogus invoice. Organizations need to be aware that a third-party supplier, vendor or other organizations outside of their security controls may have been infected.
Example: When a vendor has been infected, criminals will gain access to email accounts. They will watch email and other communications for weeks to months at a time. Once they have learned the vendor’s business processes, they will send instructions to wire money to a different location or change payment terms and they can do this in an existing email thread!
Therefore, it is critical that you have controls in place regarding how changes to invoicing and wiring can be made. A simple policy to complete a voice confirmation when any changes are requested can stop bogus invoice schemes in most cases.
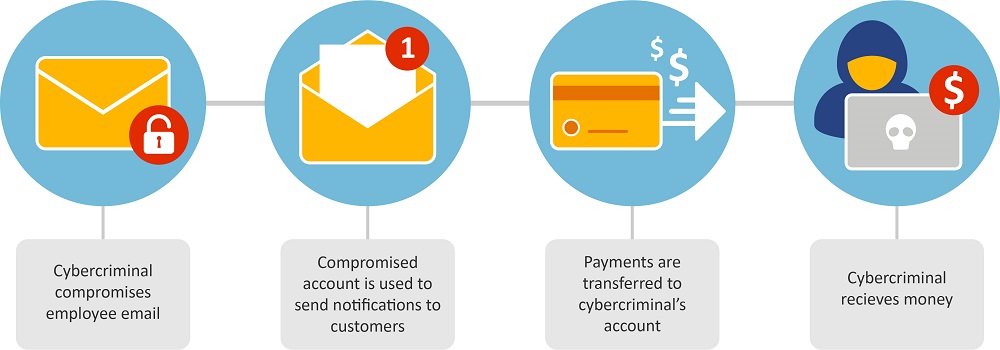
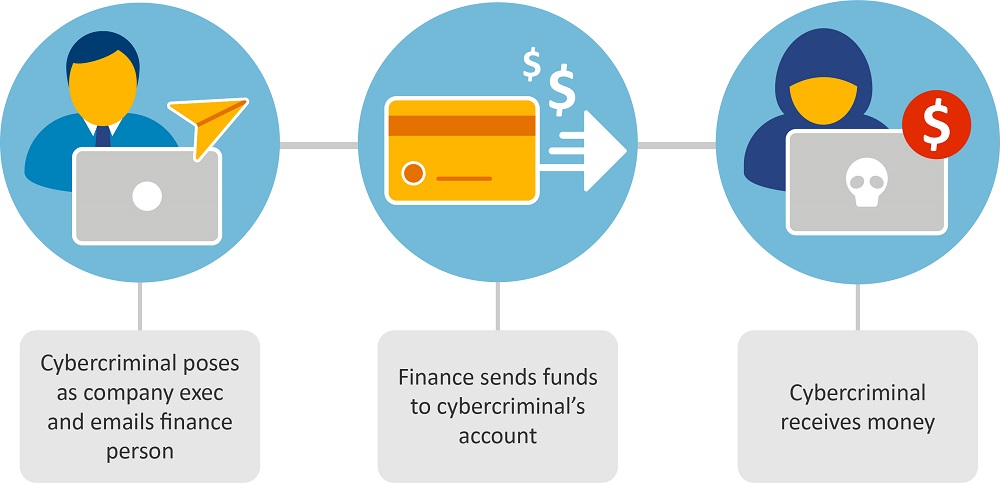
High Ranking Executive Scheme
A high-ranking executive scheme is when criminals impersonate your CEO or COO and use that deception to gain leverage within your organization. They can often find this information publicly, for example on professional networking sites, public filings and even an organization’s own website.
Managing Your Cyber Defenses
‘Reasonable’ security requires organizations to establish program ownership and enable security through a framework of technical and organizational measures. Therefore, when defining an information security program, no matter how large or small the organization, it is imperative to have someone in charge of security – whether an internal dedicated employee or a third-party consultant. This individual should document the overall cybersecurity program and utilize industry frameworks for structure. They should feel empowered to ask critical questions, such as “Do we have a complete inventory of assets? Do we have good firewalls in place? Do we have sufficient end point protection?” Don’t be the easy target!
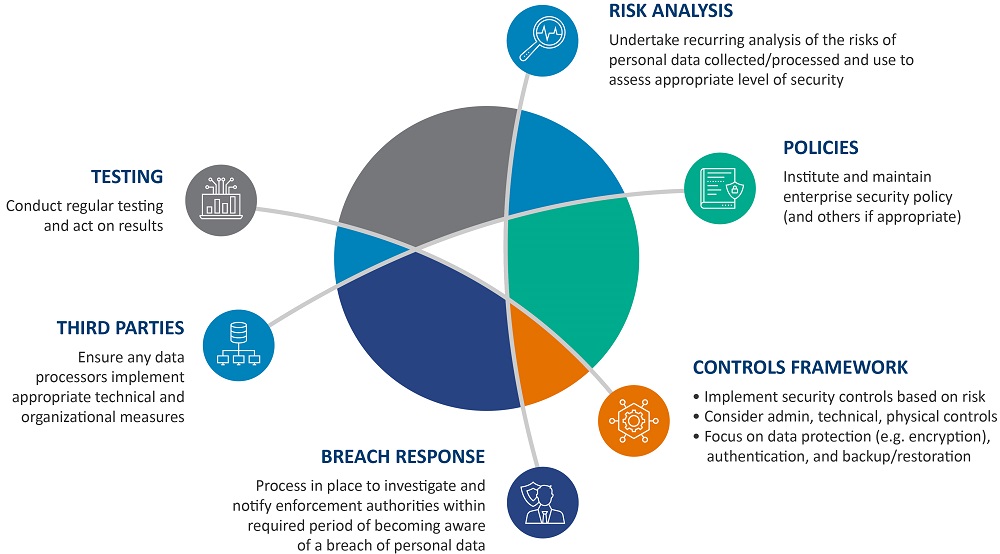
Specific controls include:
Encryption: Encryption is a highly recommended technical control used when collecting, storing, or transmitting sensitive data within and outside of the organization. For example, if you lose an encrypted laptop, the information on it, including all client information, drawings, and other sensitive information, is safe. However, it is critical to periodically evaluate the encryption solution and verify that it meets current standards.
Remote Access: Many organizations rapidly stood up or expanded their remote access capabilities during the pandemic without evaluating the cybersecurity risk of these changes. These organizations may not have the same defense capabilities, such as URL filtering, data loss prevention or Layer 7 firewalls enabled for remote assets. Therefore, it is critical to implement controls such as strong passwords and multi-factor authentication. It is important to also consider the integrity and availability of systems as part of the information security framework.
Backup: A good backup is key to being proactive about your data’s security. If an organization can efficiently restore during a ransomware attack, they are going to be in a much better position to not pay attacker demands. But the key question is how fast can they restore? Data backup from the cloud could take several days to restore, meaning days of lost productivity. Therefore, management and IT departments may want to consider additional backup options such as investment in local tape drive or local storage.
Training, training and more training: Cybercriminals will persistently prey on end users; therefore, you need thorough and ongoing training that is customized and mimics real time events. It is critical to have a method for users to report phishing attempts to IT personnel for follow-up.
To Do: Sharpen Your Response Capabilities
COVID has had a major impact on all organizations and has created a host of new challenges. If you don’t think the AEC industry is being impacted, think again. Enforce a multi-factor authentication for all remote access. If your organization rolled out VPN without it, it’s time to circle back and add it now. Start training your people and utilize security awareness training tools. Help employees identify social engineering techniques and spear-phishing emails with malicious links. Specifically, add training in regard to phishing around coronavirus and other socio-economic stressors, such as social injustice initiatives. Finally, now is the time to go beyond ‘compliance’ requirements and consider a framework-based review of your cybersecurity policies and protocols. Consider assessing your current cybersecurity posture based on a proven framework such as the Center for Internet Security (CIS) Top 20 and develop a plan of action and roadmap to reduce your vulnerabilities.
Learn More
Join Elliott Davis on May 25th for a free webinar led by Brian Kirk to discuss the latest threats and trends of cyberattacks specific to the Real Estate, Architecture, Engineering and Construction industry. Registration is available here.
About the Author
Brian Kirk is the Digital Cybersecurity Director for Elliott Davis and helps clients assess and improve their security posture through security assessments, IT budget reviews and technology implementations. Prior to joining Elliott Davis Brian was the chief information security officer at a fortune 500 engineering, design and construction firm. Brian can be reached at brian.kirk@elliottdavis.com.








